HI guys. I have Model S & Model X in the garage since new. 2015 & 2016. I've never had any issues getting map updates to either car until recently.
Both cars are attached via Wifi through our Ruckus R610. To confirm signal is not an issue I installed a 2nd AP (apple airport extreme) in the garage, that made no difference.
Both cars are able to do App commands with no delay. (honk horn etc). I recently upgraded the MS to MCU 2 and it gets about 180Mbps.
My network is sitting behind a Sonicwall TZ600. I created a "security bypass group" on the sonicwall that includes the MAC addresses for both cars so any sort of IPS, Content, spyware etc filtering is excluded on the cars.
I also have a pi-hole on the network doing DNS, but in the case of the cars, I added their mac's to the sonicwall DHCP server and assigned static IP's & google DNS to the cars.
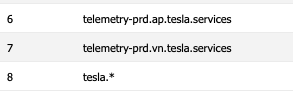
Just to be super sure, I whitelisted tesla.*
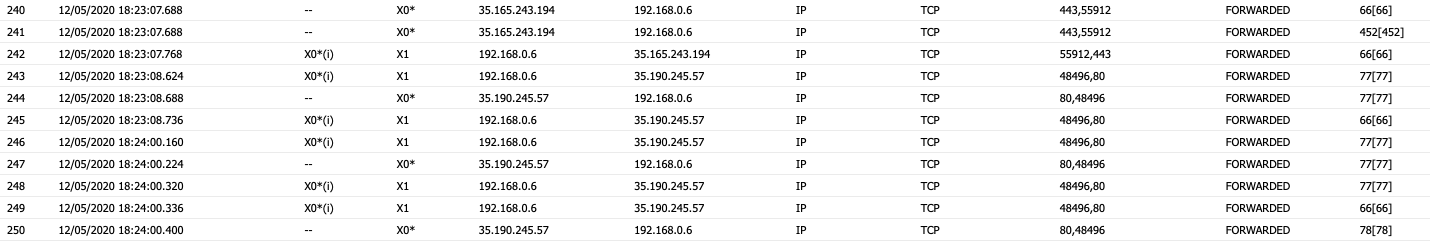
When I do a packet monitor on the sonicwall, all traffic going to/from the cars IP's is being forwarded.
If I hook the cars up to my mobile hotspot, they actually download the updates, but this is not a solution.
Any advice or tips would be greatly appreciated!!
Both cars are attached via Wifi through our Ruckus R610. To confirm signal is not an issue I installed a 2nd AP (apple airport extreme) in the garage, that made no difference.
Both cars are able to do App commands with no delay. (honk horn etc). I recently upgraded the MS to MCU 2 and it gets about 180Mbps.
My network is sitting behind a Sonicwall TZ600. I created a "security bypass group" on the sonicwall that includes the MAC addresses for both cars so any sort of IPS, Content, spyware etc filtering is excluded on the cars.
I also have a pi-hole on the network doing DNS, but in the case of the cars, I added their mac's to the sonicwall DHCP server and assigned static IP's & google DNS to the cars.
Just to be super sure, I whitelisted tesla.*
When I do a packet monitor on the sonicwall, all traffic going to/from the cars IP's is being forwarded.
If I hook the cars up to my mobile hotspot, they actually download the updates, but this is not a solution.
Any advice or tips would be greatly appreciated!!


