Cyclone
Cyclonic Member ((.oO))
OH S#!T - EVTV Friday Show - December 18, 2015 - YouTube
EVTV just published, and minute 38 there's a familiar video with a yellow Tesla in the background!
Wow that was amazingly detailed
You can install our site as a web app on your iOS device by utilizing the Add to Home Screen feature in Safari. Please see this thread for more details on this.
Note: This feature may not be available in some browsers.
OH S#!T - EVTV Friday Show - December 18, 2015 - YouTube
EVTV just published, and minute 38 there's a familiar video with a yellow Tesla in the background!
OH S#!T - EVTV Friday Show - December 18, 2015 - YouTube
EVTV just published, and minute 38 there's a familiar video with a yellow Tesla in the background!
I wonder what you can pull out of the Front cam and see the machines VisionsOk, I successfully ran Doom on the IC. Think that does it for today. lol. Screwed up my sleep schedule for sure messing around with this.
Worth noting this is a dismantle-the-car exploit...... so not super useful for non-bench stuff. I'm not taking my car apart to do this on my own vehicles... lol. But I can play CAN data to my bench and let it decode it for me.
Actually, this effort is a boon to Tesla and Owners because it gives the Owners confidence that should Tesla fail, the cars can still be updated and modified. Increased Owner confidence means that Tesla is less likely to fail because the cars have increased in value (even if it's only psychological value).
I wonder what you can pull out of the Front cam and see the machines Visions
Interesting and positive way to look at it.Actually, this effort is a boon to Tesla and Owners because it gives the Owners confidence that should Tesla fail, the cars can still be updated and modified. Increased Owner confidence means that Tesla is less likely to fail because the cars have increased in value (even if it's only psychological value).
OT: I've always wondered if TM goes under, what would happen to the Supercharger network. Would they be sold off to enterprising people to operate for a fee? Or would a larger company buy the entire network and gouge us for power?
On topic: The handshake between the SC and TM-HQ would need to be replicated or hacked on the cars if this were to happen.
Game over.
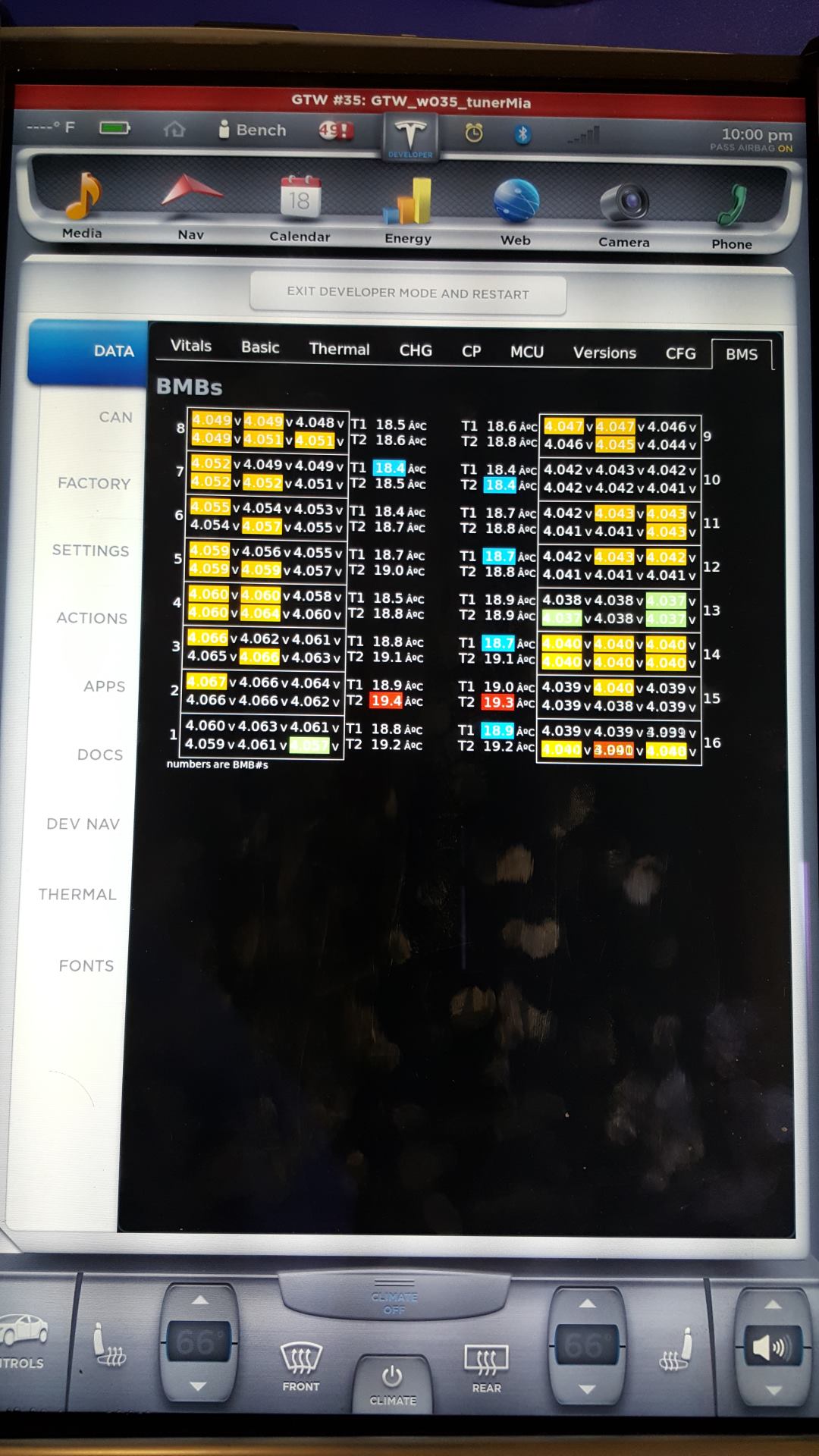
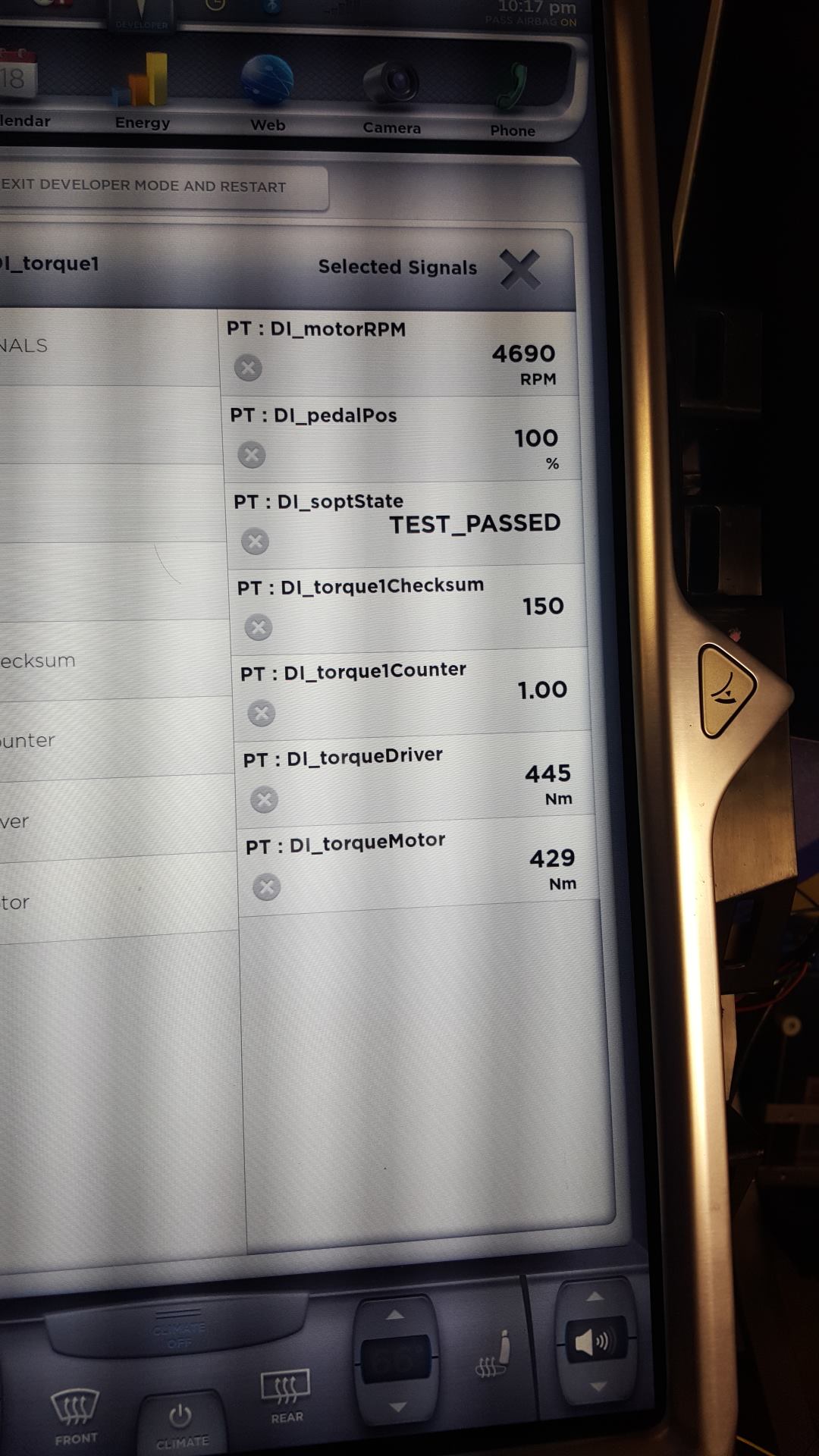
Please do not ask me how to do this just yet... while Tesla isn't patching my bench setup, I'm sure they'll patch cars in an OTA if I released how to do it publicly.
I believe one of the things factory mode does is disable the need for a key.
Andrew - Do you mean the physical fob or an auth key?
Also, the "internal use" SpCs could charge 40s and 60s that weren't enabled, so perhaps that was via a "Service Center use" mode. If so, one would hope Tesla Motors dying breath would be to put the entire network in SvC mode.
Who would pay the electric bill and maintenance and upkeep?
I would think a BMW, MB or VAG would be a higher bidder.
I'd check to see what they are using for a random number generator, it may not be so random. I assume every MCU generates it's own keys (not just the access code) but that also may not be true.Next I was working on attacking the diagnostic port security and/or the "PLEASE ENTER ACCESS CODE". Well, I figured out the access code. It's the long randomly generated 24 hour rotated security token... which is generated by the MCU and sent to Tesla via the encrypted VPN. So, no dice there for a no-disassembly exploit either. I can unlock the diagnostic port as well, but it also requires this rotating token that is impossible to offline generate (it's literally a random token generated by the MCU itself). And I also can't just blast tokens at it hoping to get the right one because it limits to one attempt per 5 seconds. Well played, Tesla. I tried a few other potential tricks to sneak some packets in, but was no good.
I'd check to see what they are using for a random number generator, it may not be so random. I assume every MCU generates it's own keys (not just the access code) but that also may not be true.
it's pretty random. And long.


