Whatever project is more interesting to you than this must be one hell of a project. I look forward to hearing about it.
It's a woman.
You can install our site as a web app on your iOS device by utilizing the Add to Home Screen feature in Safari. Please see this thread for more details on this.
Note: This feature may not be available in some browsers.
Whatever project is more interesting to you than this must be one hell of a project. I look forward to hearing about it.
Whatever project is more interesting to you than this must be one hell of a project. I look forward to hearing about it.
wk, does Tesla use 29-bit addressing for these messages? I can't think otherwise how they can stick so much distinct data into the bus.
It's a woman.
Guess I can tease.
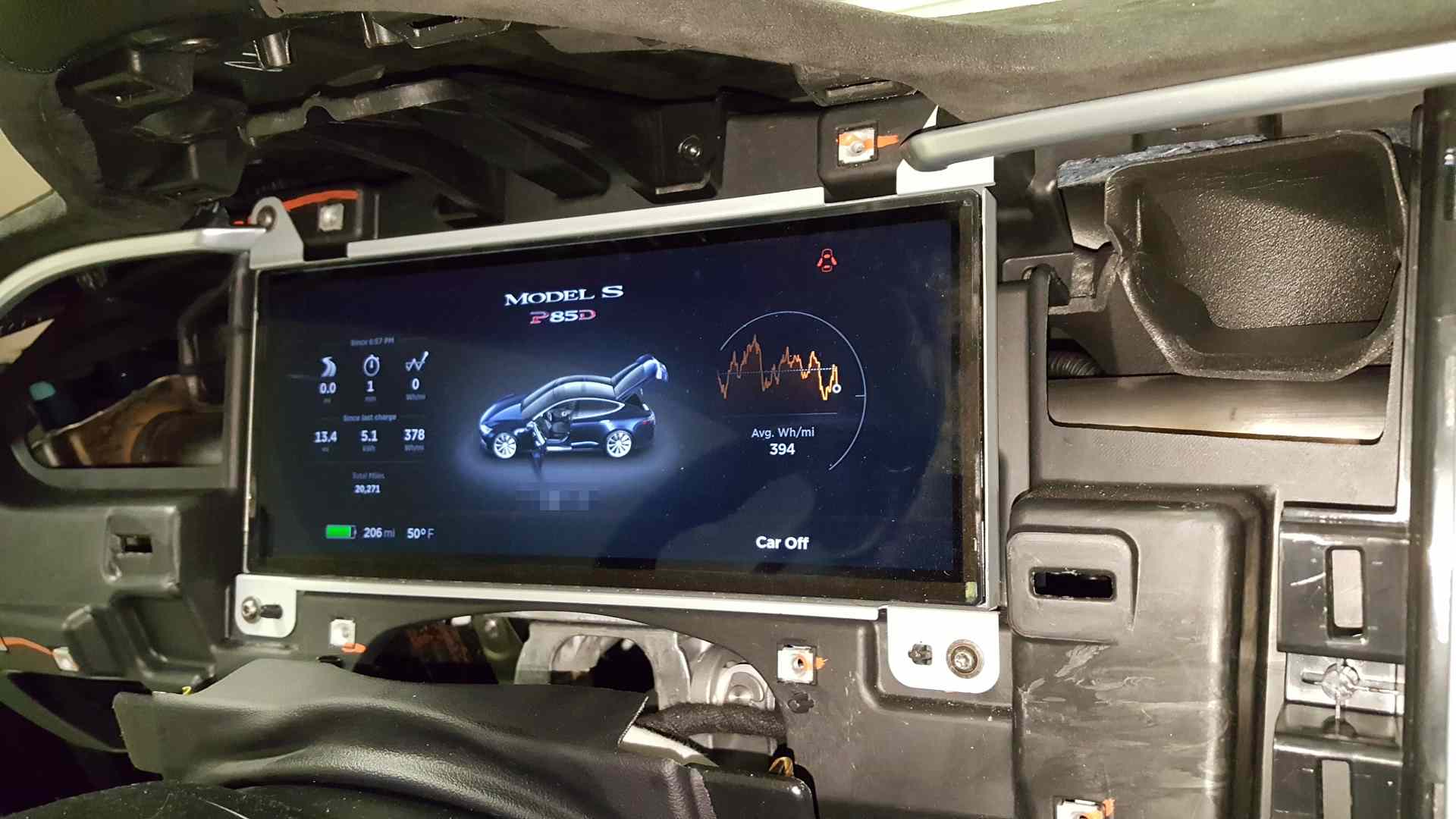
- - - Updated - - -
They do some addressing inside the 8-byte data. For example, the individual pack cell group voltages are all in one CAN ID.
Can't be, since my wife swears my projects get more attention than her. lol.
So far I've nailed down things like battery pack voltage, current, vehicle speed, cruise settings, pack temperature, individual cell group voltages, individual battery module temperatures, throttle position, and some other misc stuff. That's probably 0.01% of the data available on CAN3 alone. lol. Granted a lot of that data no one probably cares about.. I don't particularly think an owner needs the 32-bit checksum of the firmware on the fast charger control module displayed anywhere, for example... but that info is on the bus a few times per second.
I forget exactly where I spotted it on mine, but yeah probably somewhere in the CAN data. Keep in mind my bench is v6.1, so only has hidden autopilot type stuff.
15 digits starting with 8823... the cell IP when connected briefly was in the 10.0.0.0/8 range.
I like to take a more positive view to Tesla's position. The fact that Jason has been able to get this far, should really make them even more aware of potential vulnerabilities.
The bench is running 6.1, and 7 might be entirely different, but I doubt whether they ever considered anyone would go to such great lengths to figure all this out. If they are smart, they cooperate... If only to learn, and make our future cars better and safer.
Been away from this project again a bit with another project having a little more priority. Eventually I'll share the other project, but for now let's stick with this one.
That said, Tesla does make *modifying* CAN values pretty tricky. For example, there were some hacks of other cars where people flooded the CAN bus with stuff to make it do certain things. That wouldn't work nearly as easily on a Model S even with access to the CAN bus. First, most of Tesla's important CAN messages, especially ones that control things, include an extra checksum. Then, they include a counter to ensure messages are received in order. Then on top of that, on more important stuff, they include a nonce that further obfuscates the checksum and such. I haven't figured out the checksum, seems non-standard. So, if I were to do some kind of CAN attack I'd have to log hundreds of thousands of packets into a table and pull from it in order to even attempt something which would likely only be successful at most for a few packets (maybe 0.1s) before the real packets took hold again. Just speculation there, but it wouldn't even be worth trying.
\.
I've got a bunch of designs and tools left over from a past life looking at automotive ECUs. One of them is a small dongle design that was used for, among other things, reflashing tasks. It has CAN, can run off vehicle or USB power and represents itself as a mass storage class device for pulling off data. I'm working in support of wk's efforts to generate a small, inexpensive data logging capability. The device has a reasonably powerful processor and some on board flash. The goal would be to generate a logging capability that filters and discriminates so as to generate useful data files without the need for lots of post processing.
More will be coming via WK.
Cool. Basically all I'm interested is in variables related to the drivetrain. Maybe a few more than the ones you hit on to show thermal controller state (passive cooling, active heating, etc.) and that would just about wrap up my interest in the diagnostic screens.
@lola, @wk - Any plans to release a guide in the coming months to show the rest of us how to sniff and parse CAN traffic? That would be awesome!
That said, Tesla does make *modifying* CAN values pretty tricky. For example, there were some hacks of other cars where people flooded the CAN bus with stuff to make it do certain things. That wouldn't work nearly as easily on a Model S even with access to the CAN bus. First, most of Tesla's important CAN messages, especially ones that control things, include an extra checksum. Then, they include a counter to ensure messages are received in order. Then on top of that, on more important stuff, they include a nonce that further obfuscates the checksum and such. I haven't figured out the checksum, seems non-standard. So, if I were to do some kind of CAN attack I'd have to log hundreds of thousands of packets into a table and pull from it in order to even attempt something which would likely only be successful at most for a few packets (maybe 0.1s) before the real packets took hold again. Just speculation there, but it wouldn't even be worth trying.
MITM attacks on CAN devices are pretty useless too, for reasons @lolachampcar already explained, and others.
So far I've nailed down things like battery pack voltage, current, vehicle speed, cruise settings, pack temperature, individual cell group voltages, individual battery module temperatures, throttle position, and some other misc stuff. That's probably 0.01% of the data available on CAN3 alone. lol. Granted a lot of that data no one probably cares about.. I don't particularly think an owner needs the 32-bit checksum of the firmware on the fast charger control module displayed anywhere, for example... but that info is on the bus a few times per second.
I am convinced I have a duff wifi antenna or something, as at home I barely get one bar on the car when I get full strength on the phone.
It would be great if I could compare the "bars" against what dB signal strength my phone app is telling me.
tia


