Anyone out there know how to do this? As best as I can tell, the menu the tesla techs use (something to the effect of dashboard -> infotainment -> vehicle configuration change) isn't present in the version of toolbox us mere mortals get access to. However, under actions, PROC_ICE_X_SAFE-SET-VEHICLE-CONFIGS is available. The parameters it accepts are ConfigParams (type List) and Configs Require Ice Reboot (presumably yes/no, true/false, 0/1, etc -- can be left blank though I believe).
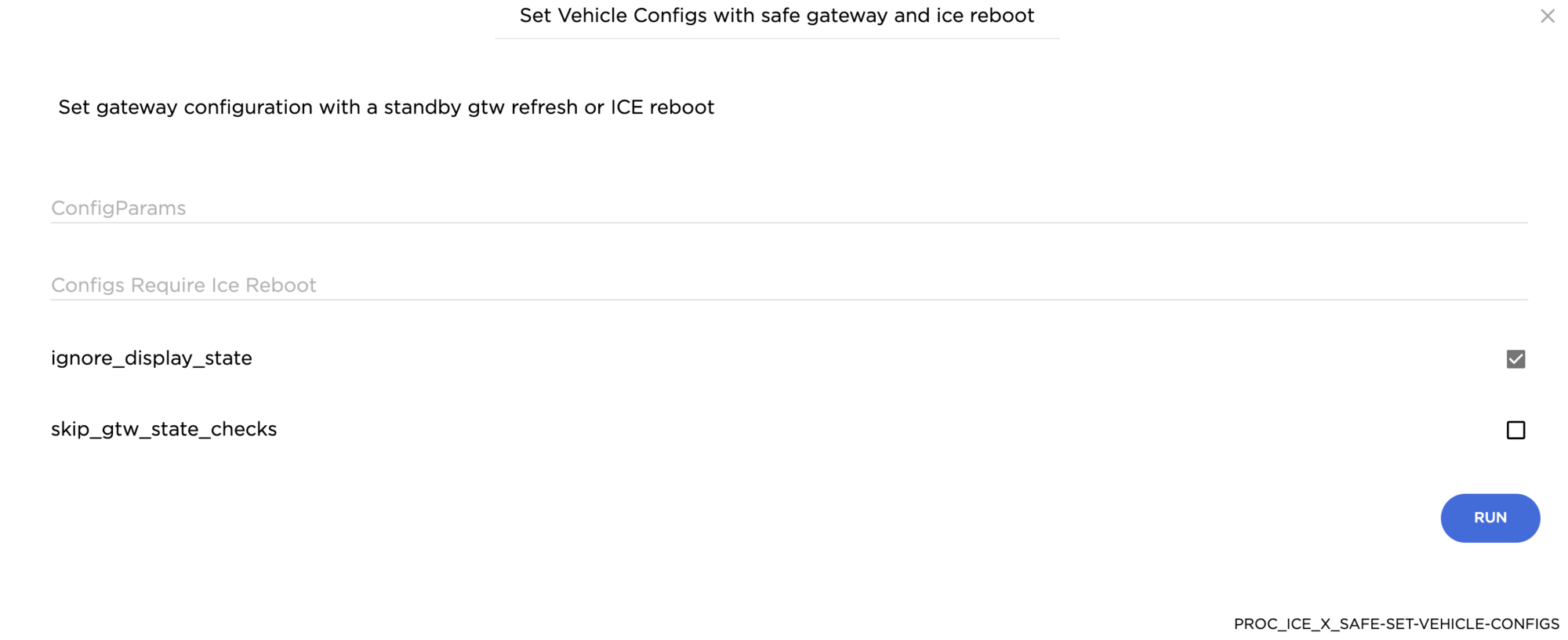
From what I can tell digging through the app.f5d3cbaebb2ad903a936.js file, this action is what's invoked when making the gateway config changes the official way. I just can't figure out how to format the input. For example I'm trying to change id 32 to 01, and I've tried sending {32, 01} and many variants (with quotes, different brackets, etc), to no avail. I mostly get an error about not being to cast the input as a List.
Anyone out there know what to do or can help with some hints? I can share any other relevant info
From what I can tell digging through the app.f5d3cbaebb2ad903a936.js file, this action is what's invoked when making the gateway config changes the official way. I just can't figure out how to format the input. For example I'm trying to change id 32 to 01, and I've tried sending {32, 01} and many variants (with quotes, different brackets, etc), to no avail. I mostly get an error about not being to cast the input as a List.
Anyone out there know what to do or can help with some hints? I can share any other relevant info



