Welcome to Tesla Motors Club
Discuss Tesla's Model S, Model 3, Model X, Model Y, Cybertruck, Roadster and More.
Register
Install the app
How to install the app on iOS
You can install our site as a web app on your iOS device by utilizing the Add to Home Screen feature in Safari. Please see this thread for more details on this.
Note: This feature may not be available in some browsers.
-
Want to remove ads? Register an account and login to see fewer ads, and become a Supporting Member to remove almost all ads.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Tesla, TSLA & the Investment World: the Perpetual Investors' Roundtable
- Thread starter AudubonB
- Start date
willow_hiller
Well-Known Member
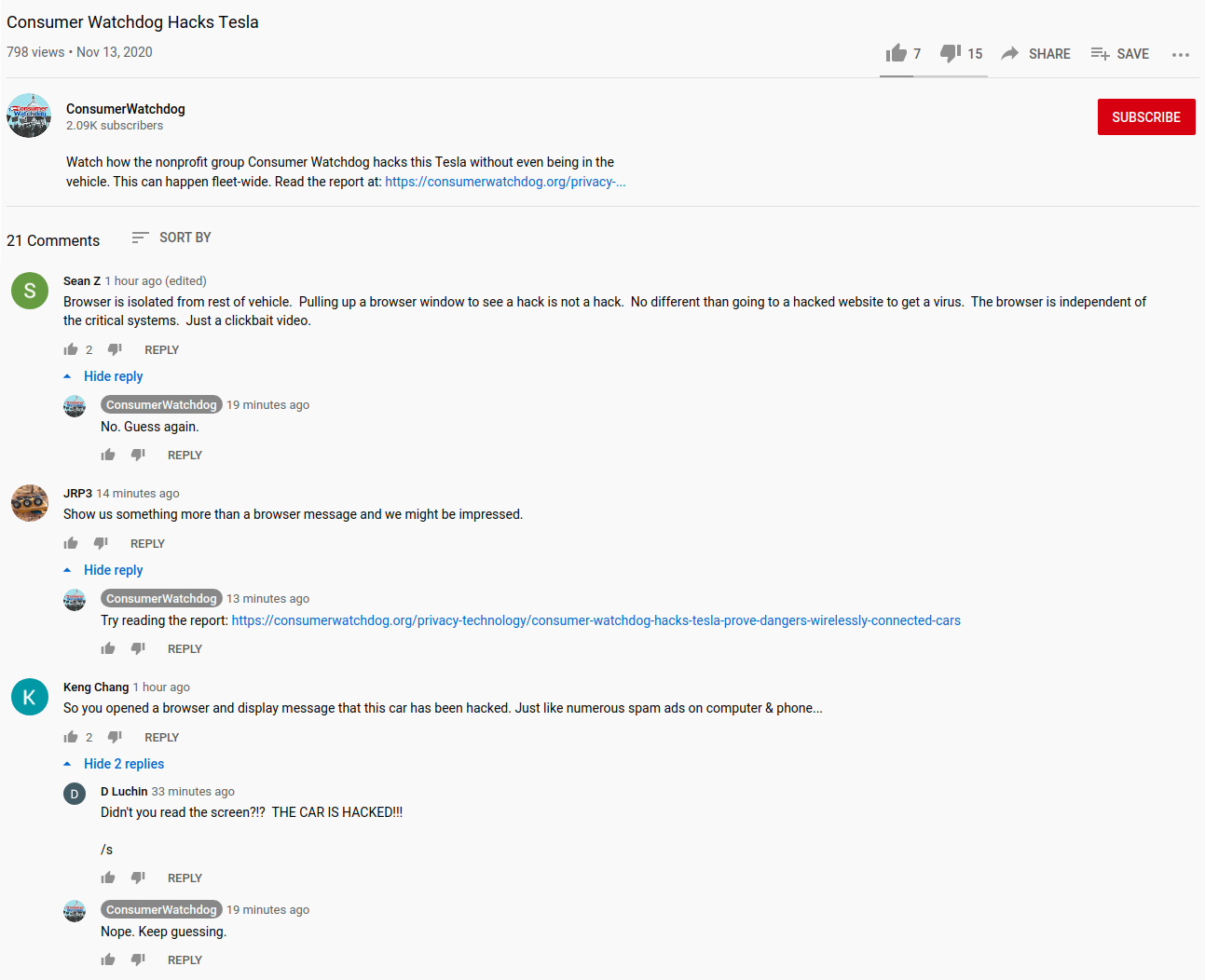
A screenshot for anyone who wants to laugh at "ConsumerWatchdog" without giving them views. Presently under 800 views, and 15 thumbs down. And they're acting rather childish in the comments:
This is probably nothing, but I'm noticing TSLA calls creeping up faster than TSLA. Could be a setup for Monday rally.
Right on. I saw a good mix of puts and call in the earlier part of the day. But this is the action in the last hour. Notice the most recent buy:
edit: times are in CST.
edit: 407.5 max pain today?
Krugerrand
Meow
Ford's CEO Farley said Friday "We are discussing (battery) cell manufacturing, I think that's natural as (EV) volume grows."
I guess they will have their terawatt factory up faster than anyone. /s
Step 2. Put together a committee to study the discussions of manufacturing batteries.
Artful Dodger
"Neko no me"
Current Prez scheduled to speak from the Rose Garden in a few minutes. Market likely positioning itself for a 'concession'. Market could see a sell off after-hrs if not. Either way, not likely to cause a large or a sustained move.This is probably nothing, but I'm noticing TSLA calls creeping up faster than TSLA. Could be a setup for Monday rally.
durkie
Member
If this was real, why would they circumvent the typical hackathon/bug bounty process?
Tesla offers up to $15,000 for a documented vulnerability that affects their vehicle fleet: Tesla’s bug bounty program | Bugcrowd
Or last year at Pwn2Own, Tesla gave away $375,000 in prize money (including a Model 3) to a team that demonstrated a browser vulnerability: Hackers conquer Tesla’s in-car web browser and win a Model 3 – TechCrunch
If this watchdog is capable of proving their exploit, what incentives did they have to turn down the bounty rewards? My guess is they cannot prove anything.
There are many compelling reasons for security researchers NOT to participate in hackathons/bug bounties. Amongst other things, when you're in a hackathon/bug bounty, the company sets all the rules, including what they consider notable, when/if you're allowed to disclose the vulnerability, and how much they'll pay. It could be possible that they think the hack is worth more on the market versus what the company would pay.
That isn't to say that any of those reasons are the case here, but still: not being in a bug bounty program (which are a very recent invention) doesn't delegitimize security research.
Bought a NIO put this am, nearly had a 50% gain at one point. I took a look at ownership, decided not to hold. Made a nice addition to my TSLA shares with the profit. Very undisciplined of me making a rare daytrade whilst breaking round trip rules in a ROTH. Now to see how long it takes the understaffed broker to spank me.
Today marks the day i officially believe GM is ahead of Tesla in the EV Market after reading this:
How General Motors Is Already Beating Tesla in China | The Motley Fool
















How General Motors Is Already Beating Tesla in China | The Motley Fool
Today marks the day i officially believe GM is ahead of Tesla in the EV Market after reading this:
View attachment 608069
How General Motors Is Already Beating Tesla in China | The Motley Fool

I’m cancelling my Motley Fool subscription! Oh wait, I already did.
bkp_duke
Well-Known Member
Custom album art?
"You've been hacked" by Firetruck Undertaker Deviants.
www.teslamotors.com does redirect.
HA HA HA HA HA
Some sysadmin got lazy and redirected the WWW site, but not the non-WWW site.
thx1139
Active Member
I dont think anyone expect any sort of concession.Current Prez scheduled to speak from the Rose Garden in a few minutes. Market likely positioning itself for a 'concession'. Market could see a sell off after-hrs if not. Either way, not likely to cause a large or a sustained move.
HA HA HA HA HA
Some sysadmin got lazy and redirected the WWW site, but not the non-WWW site.
depreciated
ssq
Member
Right on. I saw a good mix of puts and call in the earlier part of the day. But this is the action in the last hour. Notice the most recent buy:
View attachment 608059
edit: times are in CST.
edit: 407.5 max pain today?
Thanks @vikings123, where is this screen from, some brokerage?
Probably betting a rally after SpaceX's crew 1 launch.Right on. I saw a good mix of puts and call in the earlier part of the day. But this is the action in the last hour. Notice the most recent buy:
View attachment 608059
edit: times are in CST.
edit: 407.5 max pain today?
Thanks @vikings123, where is this screen from, some brokerage?
No. It's from optionflo.com. There are a number of providers that track unusual option activity and I'm checking all of them out to see who has the best real time data. flowalgo, cheddar flow are a couple of others that provide similar service, subscription ranges from 50$ to 150$ per month so very pricy but useful if you are actively trading or leveraging options.
Like always options are risky and not something I will recommend for most investors.
gabeincal
Active Member
No. It's from optionflo.com. There are a number of providers that track unusual option activity and I'm checking all of them out to see who has the best real time data. flowalgo, cheddar flow are a couple of others that provide similar service, subscription ranges from 50$ to 150$ per month so very pricy but useful if you are actively trading or leveraging options.
Like always options are risky and not something I will recommend for most investors.
Thank you for providing this useful data!
Probably betting a rally after SpaceX's crew 1 launch.
It is clear the market is ignoring Trump's posturing. This was the last 10 minutes of the market hours. Options play a big role in TSLA price action, probably the understatement of the year haha.
Sudre
Active Member
I figured we'd close between 407.50 and 410. THEY have to wait until after the Robinhood sell off so retail can't profit much from it. About an hour from close Robinhood automatically sells off everything you have that can not be covered. Once retail is out THEY can walk it around to what they want rapidly and sell what they bought/sold back from retail at profits. When an event like Robinhood's Friday sell off is that predictable THEY will use it to profit.edit: 407.5 max pain today?
Today marks the day i officially believe GM is ahead of Tesla in the EV Market after reading this:
View attachment 608069
How General Motors Is Already Beating Tesla in China | The Motley Fool

I regret that I have but one funny to give to this post.
Similar threads
- Locked
- Replies
- 0
- Views
- 3K
- Locked
- Replies
- 0
- Views
- 6K
- Locked
- Replies
- 11
- Views
- 10K
- Replies
- 6
- Views
- 5K
- Locked
- Poll
- Replies
- 1
- Views
- 12K


